RMM services are revolutionizing the way businesses manage their IT infrastructure. They offer a comprehensive suite of tools and features designed to automate, monitor, and secure your systems, freeing up your IT team to focus on strategic initiatives.
Table of Contents
From proactive monitoring and automated patching to remote access and detailed reporting, RMM services provide a centralized platform for managing your IT environment. This empowers businesses of all sizes to enhance efficiency, reduce costs, and improve overall security posture.
What are RMM Services?
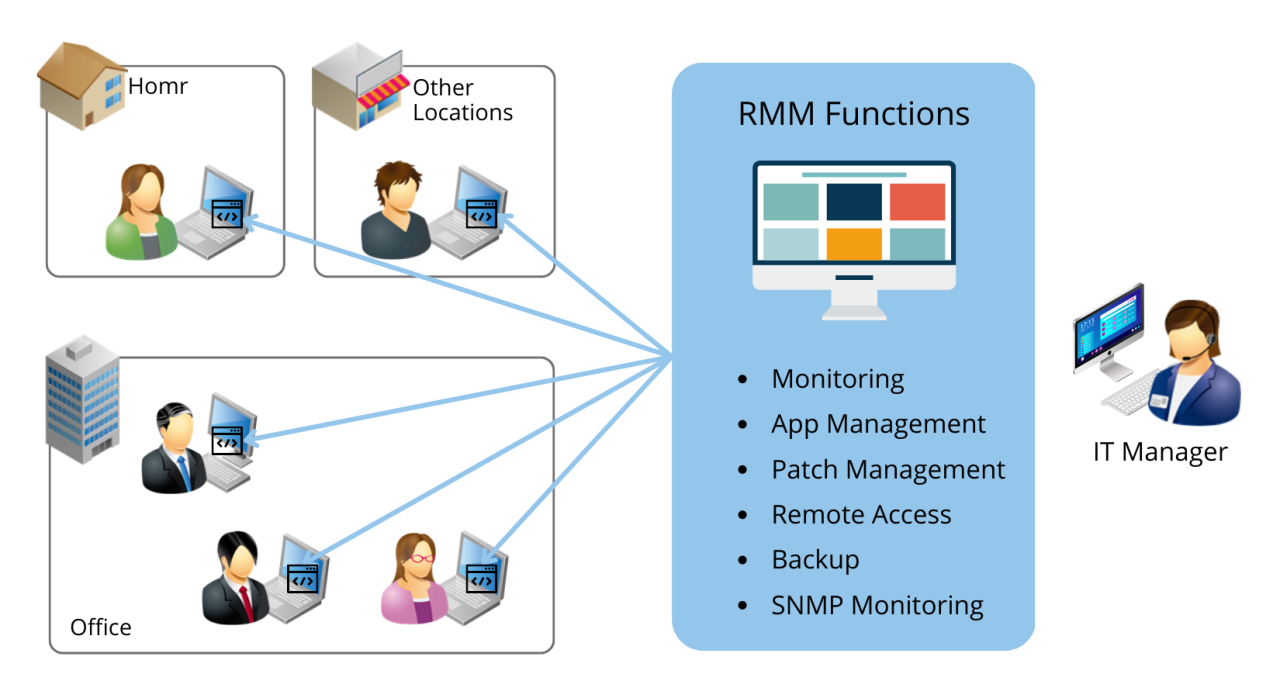
RMM (Remote Monitoring and Management) services are a suite of tools that enable IT professionals to remotely manage and monitor computer systems, networks, and other IT infrastructure. These services are designed to simplify IT administration, improve security, and enhance overall IT efficiency for businesses of all sizes.
RMM services are essential for businesses seeking to streamline their IT operations, reduce costs, and ensure the security of their data and systems. They provide a centralized platform for managing all aspects of IT infrastructure, allowing IT teams to proactively identify and resolve issues before they impact business operations.
Benefits of RMM Services
RMM services offer numerous benefits for businesses, including:
- Improved Security: RMM tools can monitor systems for vulnerabilities and malware, automatically patching systems and implementing security updates. They can also help enforce security policies, restrict access to sensitive data, and provide real-time threat detection and response.
- Increased Efficiency: RMM services automate routine tasks such as software updates, patch management, and system backups, freeing up IT staff to focus on more strategic initiatives. This can lead to significant time and cost savings.
- Enhanced Productivity: By proactively identifying and resolving issues, RMM services help ensure that systems remain operational and employees can work uninterrupted. This translates to increased productivity and reduced downtime.
- Cost Savings: RMM services can reduce IT costs by automating tasks, minimizing downtime, and preventing security breaches. They can also help optimize hardware and software utilization, leading to further cost reductions.
- Improved Compliance: RMM services can help businesses comply with industry regulations and standards by providing automated reporting and auditing capabilities. They can also ensure that systems meet specific security and compliance requirements.
Types of RMM Services
RMM services come in a variety of forms, each offering different features and functionalities. Some of the most common types of RMM services include:
- Endpoint Management: These services focus on managing and monitoring individual computers and devices, including laptops, desktops, and mobile devices. They provide tools for software deployment, patch management, inventory management, and remote control.
- Network Monitoring: These services monitor network performance, identify bottlenecks, and troubleshoot network issues. They provide real-time network performance dashboards, alerts, and reporting capabilities.
- Server Management: These services focus on managing and monitoring servers, including physical and virtual servers. They provide tools for server monitoring, performance optimization, security management, and backup and recovery.
- Security Management: These services provide comprehensive security solutions, including vulnerability scanning, malware detection, firewall management, and intrusion detection. They help businesses protect their systems from cyber threats.
- Help Desk and Support: Some RMM services include help desk and support features, providing businesses with a centralized platform for managing IT support requests. These services can automate ticket routing, track progress, and provide self-service options for common issues.
Key Features of RMM Services
RMM services offer a wide range of features to meet the specific needs of businesses. Some of the key features of RMM services include:
- Remote Monitoring and Management: RMM services allow IT professionals to monitor and manage systems remotely, providing 24/7 access to IT infrastructure.
- Automated Task Management: RMM services can automate routine tasks, such as software updates, patch management, and system backups, freeing up IT staff for more strategic work.
- Security Monitoring and Threat Detection: RMM services can monitor systems for vulnerabilities and malware, providing real-time threat detection and response capabilities.
- Performance Optimization: RMM services can monitor system performance, identify bottlenecks, and optimize resource utilization to improve system efficiency.
- Reporting and Analytics: RMM services provide detailed reporting and analytics capabilities, allowing businesses to track key metrics and gain insights into their IT infrastructure.
Key Features of RMM Services
RMM services are designed to streamline and enhance IT management, providing a wide range of features to address various challenges faced by IT professionals. These features can be categorized into key areas: security, monitoring, automation, and reporting, each contributing to a more efficient and secure IT environment.
Security
Security is paramount in today’s digital landscape. RMM solutions offer several features that strengthen security posture and protect sensitive data.
- Endpoint Security: RMM solutions integrate with antivirus software, firewalls, and intrusion detection systems to ensure endpoints are protected against malware and cyber threats. This allows for centralized management and monitoring of security policies across all devices, improving response times to potential vulnerabilities. For example, an RMM solution can automatically update antivirus definitions on all managed devices, ensuring consistent protection against the latest threats.
- Patch Management: Keeping software up-to-date is crucial for security. RMM solutions automate the process of patching operating systems and applications, minimizing the risk of exploits targeting vulnerabilities in outdated software. This proactive approach reduces the likelihood of successful attacks, as patches are applied promptly, preventing attackers from exploiting known weaknesses.
- Vulnerability Scanning: Regular vulnerability scans identify potential security weaknesses in systems and applications. RMM solutions can automate these scans, providing insights into potential vulnerabilities that need immediate attention. This allows IT professionals to prioritize remediation efforts, focusing on the most critical vulnerabilities first, minimizing the risk of exploitation.
Monitoring
Real-time monitoring of IT infrastructure is essential for proactive problem identification and resolution. RMM services provide comprehensive monitoring capabilities.
- System Performance Monitoring: RMM solutions monitor key performance indicators (KPIs) such as CPU usage, memory utilization, and disk space, providing insights into system health and potential bottlenecks. This allows IT professionals to identify performance issues early on, preventing disruptions and ensuring optimal system performance. For instance, if an RMM solution detects high CPU usage on a specific server, it can alert the IT team to investigate the cause and potentially optimize resource allocation.
- Network Monitoring: RMM services monitor network traffic, bandwidth usage, and connectivity issues, providing insights into network performance and potential problems. This allows IT professionals to identify and resolve network bottlenecks, ensuring reliable connectivity for all users. For example, an RMM solution can monitor network traffic and identify unusual patterns that might indicate a denial-of-service attack, enabling prompt mitigation measures.
- Log Management: RMM solutions centralize and analyze system logs, providing a comprehensive view of events and potential security incidents. This helps IT professionals identify patterns and anomalies, enabling faster incident response and security investigations. For example, if an RMM solution detects a suspicious login attempt from an unknown location, it can trigger an alert, allowing security personnel to investigate the incident and take appropriate action.
Automation
RMM services automate repetitive tasks, freeing up IT professionals to focus on more strategic initiatives.
- Script Execution: RMM solutions allow for the creation and execution of scripts to automate common IT tasks, such as software installation, configuration changes, and system updates. This reduces manual effort, minimizes errors, and improves efficiency. For instance, an RMM solution can automate the process of installing security patches on all managed devices, ensuring consistent and timely updates.
- Remote Access: RMM solutions provide secure remote access to managed devices, enabling IT professionals to troubleshoot issues, perform maintenance, and provide support remotely. This eliminates the need for physical presence, saving time and resources. For example, an RMM solution can enable an IT technician to remotely access a user’s computer to diagnose and resolve a software issue, without requiring the user to be physically present.
- Task Scheduling: RMM solutions allow for scheduling of tasks, such as backups, software updates, and system maintenance, ensuring these tasks are performed automatically at specific intervals. This proactive approach reduces the risk of data loss and system downtime, ensuring smooth operation. For instance, an RMM solution can schedule daily backups of critical data, ensuring data integrity and minimizing the impact of potential data loss events.
Reporting
RMM services provide comprehensive reporting capabilities, offering insights into IT infrastructure health, performance, and security.
- Performance Reports: RMM solutions generate reports on system performance, network usage, and resource utilization, providing insights into IT infrastructure health and potential areas for improvement. This allows IT professionals to identify trends and patterns, optimizing resource allocation and maximizing system efficiency.
- Security Reports: RMM solutions generate reports on security events, vulnerabilities, and compliance status, providing insights into the overall security posture of the IT environment. This allows IT professionals to identify potential risks and prioritize remediation efforts, ensuring a secure and compliant IT environment.
- Asset Management Reports: RMM solutions provide reports on hardware and software assets, including inventory details, license information, and deployment status. This allows IT professionals to track and manage assets effectively, ensuring optimal utilization and minimizing costs.
Benefits of Implementing RMM Services
RMM services offer a range of advantages for businesses of all sizes, from streamlining IT operations to enhancing security and reducing costs. By leveraging automation and centralized management, RMM solutions can significantly improve IT efficiency and overall business productivity.
Improved IT Efficiency
RMM solutions empower IT teams to manage and monitor devices and systems remotely, eliminating the need for physical presence and manual intervention. This automation frees up IT personnel to focus on more strategic tasks, such as innovation and project management.
- Automated Patch Management: RMM services automate the process of installing and updating software patches, ensuring that systems are protected against vulnerabilities and security threats. This eliminates the risk of manual errors and ensures timely patch deployment across all devices.
- Remote Monitoring and Management: RMM solutions provide real-time insights into system performance, allowing IT teams to proactively identify and address potential issues before they escalate. This reduces downtime and minimizes disruption to business operations.
- Centralized Device Management: RMM platforms offer a single console for managing all devices and systems, simplifying administration and reducing the complexity of managing diverse IT environments.
Reduced Costs
By automating tasks and streamlining IT operations, RMM services help businesses reduce their overall IT costs. This includes:
- Lower IT Labor Costs: RMM solutions free up IT staff to focus on higher-value tasks, reducing the need for additional personnel. This translates to significant savings on labor costs.
- Reduced Hardware and Software Costs: RMM services help businesses optimize their IT infrastructure by identifying underutilized resources and ensuring that devices are operating efficiently. This can lead to reductions in hardware and software costs.
- Minimized Downtime Costs: Proactive monitoring and management through RMM solutions help prevent downtime and minimize disruptions to business operations. This reduces the costs associated with lost productivity and revenue.
Enhanced Security
RMM services play a crucial role in strengthening cybersecurity posture by providing comprehensive security monitoring and management capabilities.
- Real-Time Threat Detection: RMM solutions monitor systems for suspicious activity and potential threats, providing real-time alerts and enabling prompt responses to security incidents. This helps businesses stay ahead of emerging threats and minimize the impact of security breaches.
- Endpoint Security Management: RMM platforms allow IT teams to enforce security policies and configure endpoint protection measures across all devices, ensuring that systems are adequately protected against malware and other cyber threats.
- Data Backup and Recovery: RMM solutions often include data backup and recovery capabilities, providing a safety net in case of system failures or data breaches. This ensures business continuity and minimizes the risk of data loss.
Real-World Examples
“Since implementing RMM services, our IT team has seen a significant reduction in support tickets and improved response times. The automation capabilities have freed up our staff to focus on strategic initiatives, resulting in increased productivity and innovation.” – IT Manager, Small Business
“Our company has experienced a dramatic decrease in downtime since adopting RMM solutions. The proactive monitoring and management capabilities have enabled us to identify and address potential issues before they impact our operations.” – CIO, Medium Enterprise
“RMM services have been instrumental in strengthening our cybersecurity posture. The real-time threat detection and endpoint security management features have provided us with the confidence to protect our sensitive data and critical systems.” – CISO, Large Enterprise
RMM Services and IT Automation
RMM services are designed to streamline and simplify IT management by automating repetitive tasks, ultimately freeing up IT professionals to focus on more strategic initiatives. Automation is a key feature of RMM solutions, and it plays a crucial role in enhancing efficiency and productivity within IT departments.
Benefits of Automation, Rmm services
Automation offers several advantages for IT teams using RMM services, contributing to a more efficient and effective IT environment.
- Increased Efficiency: Automating routine tasks allows IT staff to allocate their time and resources more effectively. By eliminating the need for manual intervention, automation frees up valuable time for more complex and strategic tasks, leading to improved overall efficiency.
- Reduced Errors: Human error is a common occurrence in manual processes. Automation significantly reduces the risk of human error by eliminating manual steps, ensuring consistency and accuracy in task execution.
- Improved Productivity: By automating repetitive tasks, IT teams can focus on more strategic and value-adding activities. This shift in focus leads to increased productivity and better utilization of resources.
Examples of Automated Tasks
RMM solutions can automate a wide range of tasks, significantly simplifying IT management and reducing the burden on IT staff.
- Software Updates: RMM services can automatically deploy software updates to all managed devices, ensuring that systems are always running the latest versions and benefiting from the latest security patches and bug fixes.
- System Backups: Regular system backups are essential for data protection and disaster recovery. RMM services can automate backup processes, ensuring that data is regularly backed up and readily available in case of system failures or data loss.
- Security Checks: RMM solutions can automate security checks and vulnerability assessments, identifying potential security threats and vulnerabilities across the network. This proactive approach helps to mitigate security risks and protect against cyberattacks.
- Patch Management: RMM services can automatically deploy security patches to all managed devices, ensuring that systems are protected against the latest threats and vulnerabilities. This automated approach eliminates the need for manual patching, reducing the risk of security breaches and ensuring consistent security across the network.
- Remote Monitoring: RMM solutions can monitor the performance and health of all managed devices remotely, providing real-time insights into system performance and potential issues. This proactive monitoring approach allows IT teams to identify and resolve issues before they impact users, minimizing downtime and maximizing system availability.
Case Studies and Success Stories

RMM services have proven their effectiveness in various real-world scenarios, enabling businesses to streamline IT operations, enhance security, and improve overall efficiency. This section showcases compelling case studies and success stories that demonstrate the tangible benefits of implementing RMM solutions.
Case Study: A Healthcare Provider Optimizes IT Operations
A large healthcare provider faced challenges with managing a geographically dispersed network of clinics. The IT department struggled with manual processes, inconsistent patching, and limited visibility into system performance. To address these issues, they implemented an RMM solution that provided remote monitoring and management capabilities, automated patch management, and comprehensive reporting.
Challenges Faced
- Manual IT processes, leading to inefficiencies and errors.
- Inconsistent patch management, exposing systems to vulnerabilities.
- Limited visibility into system performance and resource utilization.
Solutions Implemented
- Remote monitoring and management of all devices across the network.
- Automated patch management, ensuring timely security updates.
- Comprehensive reporting and analytics for proactive problem identification.
Outcomes Achieved
- Reduced IT support costs by 25% through automation and proactive maintenance.
- Improved security posture with consistent patch management and vulnerability detection.
- Enhanced system performance and stability through real-time monitoring and optimization.
- Increased IT staff productivity, freeing them to focus on strategic initiatives.
“The implementation of RMM services has been a game-changer for our IT operations. We have significantly improved efficiency, reduced downtime, and enhanced security, allowing us to focus on delivering better patient care.” – IT Director, Healthcare Provider
Case Study: A Retail Chain Improves Security and Compliance
A national retail chain with numerous store locations faced significant security challenges. The IT infrastructure was vulnerable to cyberattacks, and maintaining compliance with industry regulations was a constant struggle. To mitigate these risks, they adopted an RMM solution that provided endpoint security, vulnerability scanning, and automated compliance reporting.
Challenges Faced
- Vulnerable IT infrastructure, exposing sensitive data to cyber threats.
- Difficulty in maintaining compliance with industry regulations.
- Limited resources for security monitoring and incident response.
Solutions Implemented
- Endpoint security software to protect against malware and unauthorized access.
- Automated vulnerability scanning to identify and remediate security weaknesses.
- Compliance reporting to demonstrate adherence to industry standards.
Outcomes Achieved
- Reduced security incidents by 70% through proactive threat detection and mitigation.
- Simplified compliance reporting and reduced audit preparation time.
- Improved overall security posture, safeguarding customer data and business operations.
“RMM services have been instrumental in strengthening our security posture and ensuring compliance with industry regulations. We have gained peace of mind knowing that our systems are protected and our data is secure.” – CIO, Retail Chain
Last Word
As the IT landscape continues to evolve, RMM services are becoming increasingly crucial for businesses seeking to maintain a competitive edge. By leveraging the power of automation, remote management, and robust security features, RMM solutions empower businesses to achieve greater efficiency, optimize resource allocation, and safeguard their digital assets against evolving threats.
RMM services are a great way to streamline your IT operations, but sometimes you need to convert a PDF document to an AutoCAD drawing. If you’re facing this challenge, you can utilize a handy online tool like pdf to autocad to quickly and efficiently convert your files.
Once you’ve got your drawing in the right format, you can easily incorporate it into your RMM workflow, ensuring seamless integration and a smooth workflow.
