Network RMM, or Remote Monitoring and Management, is a powerful tool for businesses of all sizes to streamline their IT operations. It provides a centralized platform for managing and monitoring devices, applications, and networks, empowering IT teams to proactively identify and resolve issues before they impact users.
Table of Contents
By automating tasks, reducing manual intervention, and providing real-time insights, Network RMM solutions enable organizations to optimize IT efficiency, enhance security posture, and improve overall business performance.
What is Network RMM?
Network RMM (Remote Monitoring and Management) is a powerful tool that allows IT professionals to remotely monitor and manage their clients’ networks and devices. It enables centralized control over endpoints, ensuring smooth operations and proactive security.
Core Functionalities of Network RMM
Network RMM solutions offer a comprehensive set of features that streamline IT management tasks. Here are some of the core functionalities:
- Endpoint Monitoring: Network RMM solutions provide real-time monitoring of endpoints, including servers, workstations, and mobile devices. This allows IT teams to identify potential issues before they impact users.
- Patch Management: Automated patch management ensures that all devices are kept up-to-date with the latest security updates, reducing the risk of vulnerabilities and attacks.
- Software Deployment: Network RMM simplifies software deployment by enabling the remote installation and configuration of applications across multiple devices.
- Security Management: Network RMM solutions incorporate security features such as antivirus protection, firewall management, and intrusion detection to safeguard devices and data.
- Remote Control: Network RMM enables remote access and control of endpoints, allowing IT professionals to troubleshoot issues and perform maintenance tasks from a central location.
- Reporting and Analytics: Network RMM solutions generate detailed reports and analytics that provide insights into network performance, security posture, and user activity.
Benefits of Using Network RMM Solutions
Network RMM solutions offer numerous benefits to IT professionals and organizations:
- Improved Efficiency: Network RMM automates many IT tasks, freeing up IT professionals to focus on strategic initiatives.
- Enhanced Security: Proactive security measures like automated patching and vulnerability scanning help mitigate security risks.
- Reduced Costs: Network RMM can lower IT operational costs by minimizing downtime and reducing the need for on-site support.
- Increased Productivity: Network RMM ensures that devices are running smoothly, minimizing user downtime and improving productivity.
- Scalability: Network RMM solutions can easily scale to accommodate growing IT environments.
Types of Network RMM Solutions
Network RMM solutions are available in various formats, each with its own advantages:
- Cloud-Based RMM: Cloud-based solutions are hosted on a third-party cloud platform, providing access from anywhere with an internet connection. They offer high scalability and flexibility.
- On-Premises RMM: On-premises solutions are installed and managed within an organization’s own infrastructure. They offer greater control over data security and privacy.
Benefits of Implementing Network RMM
Implementing a Network RMM solution can significantly enhance your IT operations, providing a robust framework for managing and securing your network infrastructure. Network RMM solutions offer a wide range of benefits that can streamline your IT processes, improve security posture, and optimize resource allocation.
Increased IT Efficiency and Productivity
Network RMM tools automate routine tasks, freeing up valuable time for your IT team to focus on more strategic initiatives. By automating repetitive tasks, such as software updates, patch management, and system monitoring, Network RMM solutions reduce the burden on IT staff, enabling them to work more efficiently and productively.
- Automated Patch Management: Network RMM solutions automate the process of identifying, downloading, and installing security patches for all devices on your network, ensuring that systems are always up-to-date and protected against vulnerabilities.
- Remote System Monitoring: Network RMM tools provide real-time visibility into the health and performance of all devices on your network, enabling proactive issue detection and resolution. This eliminates the need for manual checks and allows IT staff to address issues before they escalate into major problems.
- Automated Software Deployment: Network RMM solutions simplify the process of deploying software updates and new applications across your network. This ensures that all devices have the latest software versions and reduces the time and effort required for manual deployments.
Improved Security Posture and Threat Mitigation
Network RMM solutions play a crucial role in enhancing your organization’s security posture and mitigating potential threats. By providing comprehensive monitoring, vulnerability scanning, and security policy enforcement capabilities, Network RMM tools help you identify and address security risks before they can compromise your network.
- Real-time Security Monitoring: Network RMM solutions provide constant monitoring of your network for suspicious activity, including unauthorized access attempts, malware infections, and other security threats. This real-time visibility allows you to respond quickly to incidents and prevent potential breaches.
- Vulnerability Scanning and Remediation: Network RMM tools regularly scan your network for vulnerabilities, such as outdated software, misconfigured settings, and open ports. This proactive approach helps you identify and address security weaknesses before they can be exploited by attackers.
- Security Policy Enforcement: Network RMM solutions allow you to enforce security policies across your network, ensuring that all devices adhere to your organization’s security standards. This includes password complexity requirements, firewall configurations, and access control settings.
Reduced Operational Costs and Improved ROI
By automating tasks, streamlining workflows, and reducing the risk of security breaches, Network RMM solutions can significantly reduce your organization’s operational costs and improve return on investment.
- Reduced IT Labor Costs: Network RMM solutions automate many routine tasks, freeing up your IT team to focus on more strategic initiatives. This reduces the need for additional IT staff and lowers labor costs.
- Minimized Downtime and Service Interruptions: Network RMM tools proactively identify and resolve issues, reducing downtime and service interruptions. This minimizes the impact on your business operations and improves productivity.
- Improved Security Posture and Reduced Risk: By strengthening your security posture and mitigating threats, Network RMM solutions reduce the risk of costly security breaches and data loss. This can significantly reduce your organization’s financial exposure and protect your valuable assets.
Choosing the Right Network RMM Solution
Selecting the right Network RMM solution is crucial for any organization looking to streamline IT operations, enhance security, and improve overall network performance. The right solution can automate tasks, reduce downtime, and provide valuable insights into your network health. However, choosing the right solution from the many available options can be daunting.
Vendor Comparison and Offerings
Network RMM vendors offer a wide range of features and functionalities, each tailored to specific needs and budgets. Comparing and contrasting different vendors and their offerings is essential to find the solution that best aligns with your requirements.
- Features: Consider the core features offered by each vendor, such as remote access, patch management, endpoint security, asset management, and reporting. Evaluate if the features meet your specific needs and align with your IT goals.
- Pricing: Network RMM solutions are priced differently, with options ranging from flat monthly fees to per-device pricing. Analyze the pricing models and determine the most cost-effective option for your organization’s budget.
- Scalability: Ensure the chosen solution can scale with your organization’s growth. Consider the number of devices, users, and locations you manage and select a solution that can accommodate future expansion.
- Integration: Check if the solution integrates with your existing IT infrastructure and other tools, such as your help desk software or security information and event management (SIEM) system. Seamless integration can streamline workflows and reduce redundancy.
- Support: Assess the level of technical support offered by each vendor. Look for solutions with responsive customer service, comprehensive documentation, and regular updates to ensure smooth operations.
Key Factors to Consider
Beyond vendor offerings, several key factors should guide your decision-making process when choosing a Network RMM solution.
- Network Size and Complexity: For small businesses with a simple network, a basic solution may suffice. However, larger organizations with complex networks require more advanced features and capabilities.
- Security Requirements: Evaluate your security needs and choose a solution that offers robust security features like endpoint protection, vulnerability scanning, and multi-factor authentication. Consider compliance requirements and choose a solution that aligns with industry standards and regulations.
- IT Team Expertise: Factor in the technical expertise of your IT team. Choose a solution that is user-friendly and provides adequate training resources for your team to manage the solution effectively.
- Budget: Determine your budget and consider the cost of the solution, including implementation, training, and ongoing maintenance. Evaluate the return on investment (ROI) and ensure the solution provides value for your investment.
- Future Growth: Consider your organization’s future growth plans and choose a solution that can scale with your needs. Select a solution that offers flexibility and allows for future expansion without significant disruptions.
Evaluation Checklist
A comprehensive evaluation checklist can help you make an informed decision. Consider the following factors:
- Features and Functionality: Does the solution offer the features you need, such as remote access, patch management, endpoint security, asset management, and reporting?
- Ease of Use: Is the solution user-friendly and intuitive for your IT team?
- Scalability and Flexibility: Can the solution scale with your organization’s growth and adapt to future changes?
- Integration: Does the solution integrate with your existing IT infrastructure and other tools?
- Security: Does the solution offer robust security features and comply with industry standards and regulations?
- Pricing and Value: Is the solution cost-effective and provides value for your investment?
- Support and Documentation: Does the vendor offer responsive customer service, comprehensive documentation, and regular updates?
- Vendor Reputation: Research the vendor’s reputation and customer reviews to assess their reliability and track record.
Network RMM Implementation and Deployment
Implementing a Network RMM solution can significantly enhance your IT infrastructure’s efficiency and security. This section will guide you through the steps involved in implementing a Network RMM solution, discuss best practices for integrating it with your existing IT infrastructure, and provide recommendations for configuring and customizing the solution.
Steps Involved in Implementing a Network RMM Solution
Implementing a Network RMM solution involves a series of steps, each crucial to ensuring a smooth and successful deployment.
- Needs Assessment and Planning: Begin by identifying your specific IT management needs. What are your pain points? What tasks do you want to automate? What level of security do you require? Once you have a clear understanding of your needs, you can start planning the implementation process. This includes defining your scope, identifying your target devices, and choosing the right Network RMM solution for your organization.
- Solution Selection: Selecting the right Network RMM solution is crucial for your success. Consider factors such as features, pricing, scalability, ease of use, and compatibility with your existing IT infrastructure. Evaluate different solutions, request demos, and read reviews from other users to make an informed decision.
- Installation and Configuration: Once you have chosen a solution, you will need to install it on your network. This usually involves installing an agent on each device you want to manage. After installation, configure the solution to meet your specific requirements. This may involve setting up policies, creating alerts, and customizing reports.
- Agent Deployment: Deploying the RMM agent on your network devices is a crucial step. Consider methods such as manual installation, group policy deployment, or scripting.
- Integration with Existing IT Infrastructure: Integrating the Network RMM solution with your existing IT infrastructure, such as your Active Directory or help desk ticketing system, can streamline your workflows and provide a more unified management experience.
- Testing and Optimization: After deploying the Network RMM solution, thoroughly test its functionality and make any necessary adjustments. This includes testing patch management, remote control, and other features. Ensure that the solution is working as expected and that it meets your requirements.
- Training and Support: Provide training to your IT team on how to use the Network RMM solution. This will help them understand its features and maximize its benefits. Ensure that you have access to ongoing support from the Network RMM vendor.
- Monitoring and Maintenance: Continuously monitor the performance of your Network RMM solution and make necessary adjustments to ensure optimal performance. This includes updating the solution and its agents regularly.
Best Practices for Integrating Network RMM with Existing IT Infrastructure
Successfully integrating a Network RMM solution with your existing IT infrastructure is vital for maximizing its benefits.
- Identify Existing Systems and Tools: Before integration, carefully document your existing IT infrastructure, including hardware, software, and network devices. This will help you understand potential compatibility issues and identify areas where the Network RMM solution can complement your existing systems.
- Leverage APIs: Many Network RMM solutions offer APIs (Application Programming Interfaces) that allow them to integrate with other systems. Use these APIs to connect your Network RMM solution to your help desk ticketing system, asset management database, or other tools.
- Automate Tasks: Automate as many tasks as possible to reduce manual effort and improve efficiency. For example, use the Network RMM solution to automate software updates, patch management, and other routine tasks.
- Centralized Reporting: Centralize reporting to gain a comprehensive view of your IT infrastructure. The Network RMM solution can provide insights into device health, security vulnerabilities, and other key metrics.
- Data Security: Prioritize data security during integration. Ensure that the Network RMM solution is compliant with relevant security standards and that your data is protected.
Configuring and Customizing a Network RMM Solution
Configuring and customizing a Network RMM solution allows you to tailor it to your specific needs and optimize its performance.
- Policy Creation: Create policies to enforce security settings, manage software updates, and control user access. These policies can be applied to individual devices or groups of devices.
- Alerting and Notifications: Configure alerts and notifications to receive timely information about critical events, such as security breaches, hardware failures, or software updates. Customize notification channels, such as email, SMS, or in-app notifications.
- Reporting and Dashboards: Create custom reports and dashboards to visualize key performance indicators (KPIs) and gain insights into your IT infrastructure. These reports can help you identify trends, make informed decisions, and improve your overall IT management.
- User Roles and Permissions: Implement a role-based access control system to manage user permissions and ensure that only authorized individuals have access to sensitive information.
- Remote Control and Access: Configure remote control features to access and manage devices remotely. This can be useful for troubleshooting issues, deploying software, or providing technical support.
Future Trends in Network RMM
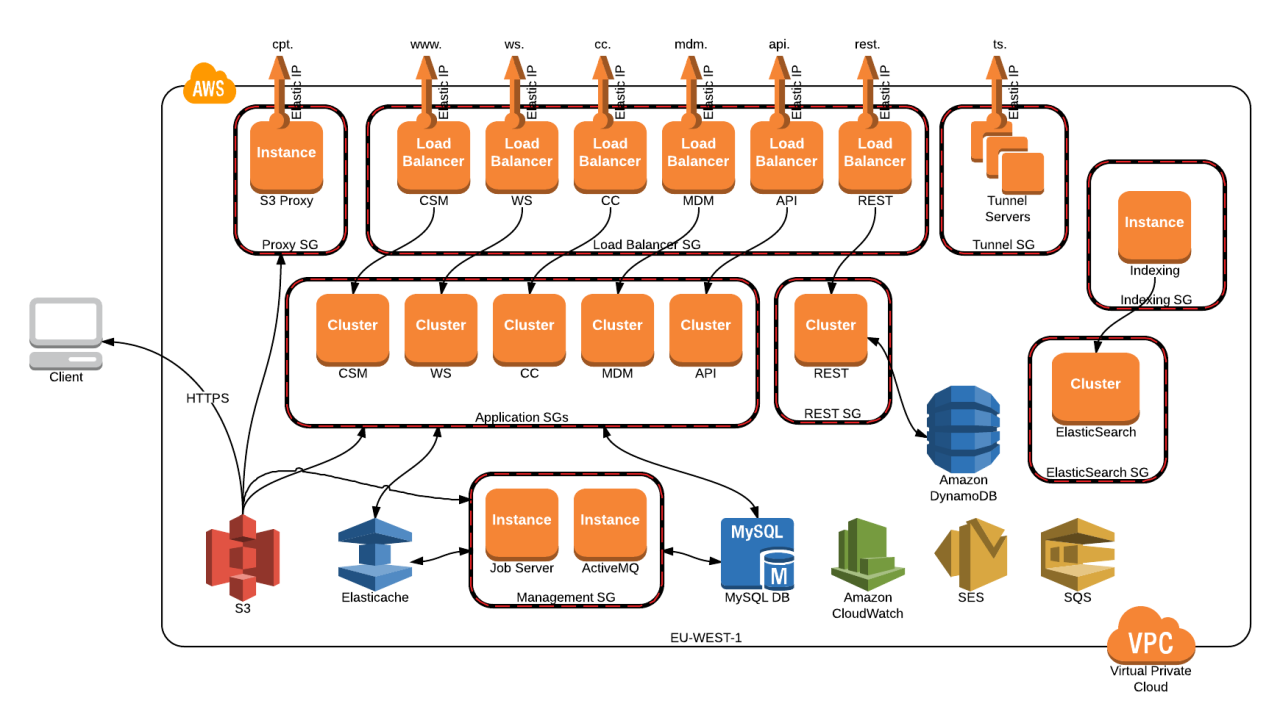
The landscape of Network RMM is constantly evolving, driven by advancements in technology and the changing demands of modern IT environments. Emerging technologies like cloud computing, artificial intelligence (AI), and automation are playing a significant role in shaping the future of Network RMM.
Impact of Cloud Computing
Cloud computing has fundamentally transformed the way businesses operate, and its impact on Network RMM is undeniable. Cloud-based Network RMM solutions offer numerous advantages over traditional on-premises solutions, including:
- Scalability and Flexibility: Cloud-based solutions can easily scale to meet the growing needs of businesses, providing access to resources on demand. This flexibility allows businesses to adapt quickly to changing requirements without investing in expensive hardware upgrades.
- Cost-Effectiveness: Cloud-based solutions eliminate the need for expensive hardware and software investments, reducing overall costs. Businesses can pay for only the resources they use, making it a cost-effective option.
- Accessibility: Cloud-based solutions can be accessed from anywhere with an internet connection, providing remote access to IT resources and enabling remote management and monitoring.
- Enhanced Security: Cloud providers invest heavily in security infrastructure and expertise, providing robust security measures that are often more advanced than those available to individual businesses.
As cloud adoption continues to grow, we can expect to see more cloud-native Network RMM solutions emerge, offering seamless integration with cloud platforms and enhanced functionality for managing cloud-based infrastructure.
Impact of AI and Automation
AI and automation are revolutionizing various industries, and Network RMM is no exception. AI-powered tools can analyze vast amounts of data to identify patterns and anomalies, providing valuable insights into system health and performance. Automation tools can streamline repetitive tasks, freeing up IT professionals to focus on more strategic initiatives.
- Proactive Monitoring and Troubleshooting: AI algorithms can analyze real-time data from network devices and applications to identify potential issues before they escalate. This proactive approach helps prevent downtime and improves system stability.
- Automated Patch Management: AI-powered automation can identify and deploy security patches across the network, reducing the risk of vulnerabilities and improving overall security posture.
- Predictive Maintenance: AI algorithms can analyze historical data to predict potential hardware failures, enabling IT professionals to proactively replace or repair components before they cause disruptions.
As AI and automation technologies continue to advance, we can expect to see more sophisticated and intelligent Network RMM solutions that can handle increasingly complex tasks and provide deeper insights into network performance and security.
Future of Network RMM
The future of Network RMM is bright, with exciting advancements on the horizon. The convergence of cloud computing, AI, and automation will create a new generation of Network RMM solutions that are more intelligent, efficient, and proactive.
- Increased Integration: Network RMM solutions will become more tightly integrated with other IT tools and services, creating a comprehensive ecosystem for managing and monitoring IT infrastructure.
- Enhanced Security: Network RMM solutions will play a crucial role in protecting networks from increasingly sophisticated cyber threats. AI-powered security features will help identify and mitigate threats in real-time, enhancing overall security posture.
- Personalized Experiences: Network RMM solutions will offer personalized experiences tailored to the specific needs of individual businesses. This will involve using AI to analyze data and provide customized recommendations for optimizing network performance and security.
Network RMM will continue to evolve, playing a vital role in modern IT environments. By embracing emerging technologies, businesses can leverage Network RMM solutions to improve network performance, enhance security, and drive business success.
Case Studies and Success Stories
Network RMM solutions have proven their worth across various industries, offering tangible benefits to businesses of all sizes. These real-world examples demonstrate how Network RMM can streamline IT operations, improve efficiency, and enhance overall business performance.
Impact of Network RMM on Business Outcomes
This section delves into how Network RMM can impact business outcomes. Organizations that implement Network RMM solutions often experience significant improvements in key areas, leading to increased productivity, reduced costs, and enhanced security.
- Improved IT Service Delivery: Network RMM enables IT teams to proactively monitor and manage devices, ensuring smooth operation and timely resolution of issues. This translates to improved service delivery, reduced downtime, and enhanced user satisfaction.
- Reduced IT Costs: Network RMM automates tasks, streamlines workflows, and minimizes manual intervention. This leads to reduced labor costs, lower hardware maintenance expenses, and optimized resource allocation.
- Enhanced Security Posture: Network RMM solutions offer robust security features, including vulnerability scanning, patch management, and endpoint protection. This strengthens the overall security posture, reducing the risk of cyberattacks and data breaches.
Real-World Examples of Network RMM Implementation
Let’s explore real-world examples of organizations that have successfully implemented Network RMM solutions.
- Case Study: A Healthcare Provider: A large healthcare provider implemented a Network RMM solution to manage its vast network of medical devices. The solution enabled the organization to monitor device performance, proactively identify and resolve issues, and ensure patient safety by maintaining device compliance with industry regulations.
- Case Study: A Financial Institution: A financial institution deployed a Network RMM solution to enhance its security posture and protect sensitive customer data. The solution automated patch management, vulnerability scanning, and endpoint security measures, significantly reducing the risk of cyberattacks and data breaches.
- Case Study: A Retail Chain: A retail chain implemented a Network RMM solution to streamline IT operations and improve the customer experience. The solution automated tasks such as software updates, hardware maintenance, and network monitoring, ensuring a smooth and efficient operation of point-of-sale systems and other critical infrastructure.
Benefits and Challenges Experienced by Organizations Using Network RMM Solutions
Organizations using Network RMM solutions often encounter both benefits and challenges.
- Benefits:
- Improved Efficiency and Productivity: Network RMM automates tasks, freeing up IT staff to focus on strategic initiatives and complex problem-solving.
- Enhanced Security and Compliance: Network RMM solutions provide robust security features and automation tools, ensuring compliance with industry regulations and reducing the risk of cyberattacks.
- Reduced Downtime and Improved Service Delivery: Network RMM enables proactive monitoring and management of devices, minimizing downtime and improving service delivery to users.
- Centralized Management and Control: Network RMM provides a single platform for managing and monitoring all devices, simplifying IT operations and enhancing control over the IT environment.
- Challenges:
- Implementation Complexity: Implementing a Network RMM solution can be complex, requiring careful planning and configuration.
- Integration with Existing Systems: Integrating the Network RMM solution with existing IT systems and applications can pose challenges.
- Cost of Implementation: The cost of implementing and maintaining a Network RMM solution can be significant, depending on the size and complexity of the IT environment.
- Training and Support: IT staff may require training to effectively use the Network RMM solution, and ongoing support may be needed.
Network RMM Security Considerations
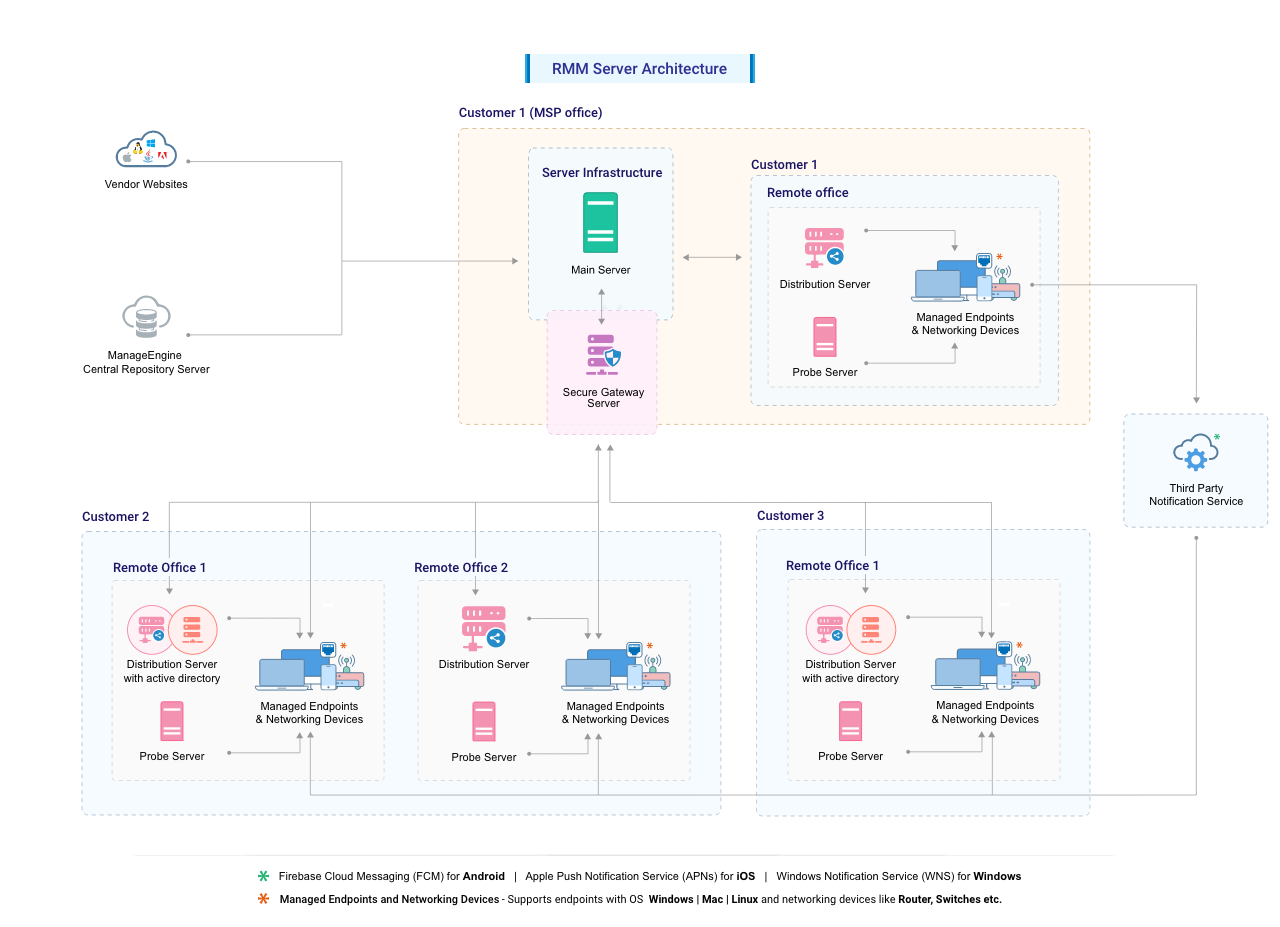
Network RMM solutions are essential for managing and securing modern IT environments. However, their very nature – granting remote access to critical systems – necessitates careful consideration of security implications.
Security Vulnerabilities and Mitigation
Network RMM solutions are not immune to security vulnerabilities. Potential threats can include unauthorized access, data breaches, and malware infections. It’s crucial to implement robust security measures to mitigate these risks.
- Strong Authentication: Implement multi-factor authentication (MFA) for all user accounts, including administrators. This adds an extra layer of security by requiring users to provide two or more forms of identification before granting access.
- Access Control: Use role-based access control (RBAC) to limit user privileges to only what they need to perform their duties. This ensures that even if an account is compromised, the attacker’s access is restricted.
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities. This includes scanning for known vulnerabilities, reviewing security logs, and testing security controls.
- Encryption: All data transmitted between the RMM server and agents should be encrypted using industry-standard protocols like TLS/SSL. This ensures that data cannot be intercepted or read by unauthorized parties.
- Secure Software Updates: Keep the RMM software, agents, and all connected systems up-to-date with the latest security patches and updates. This is essential to protect against newly discovered vulnerabilities.
- Security Awareness Training: Train all users on best practices for security, including strong password creation, phishing awareness, and how to identify suspicious emails or websites.
Network RMM and Overall Network Security
Network RMM solutions can play a significant role in enhancing overall network security posture.
- Proactive Vulnerability Management: Network RMM tools can automatically scan for vulnerabilities on managed devices and provide alerts for potential threats. This enables organizations to take proactive steps to patch vulnerabilities before they can be exploited.
- Real-Time Threat Detection: Network RMM solutions can monitor systems for suspicious activity and alert administrators to potential security incidents. This includes monitoring for malware infections, unauthorized access attempts, and other anomalous behavior.
- Centralized Security Policy Management: Network RMM tools can be used to enforce security policies across the entire network, ensuring that all devices meet minimum security standards. This includes enforcing strong password policies, disabling unnecessary services, and implementing other security best practices.
- Automated Security Tasks: Network RMM solutions can automate repetitive security tasks, such as software updates, antivirus scans, and firewall configuration. This frees up security professionals to focus on more strategic tasks.
Network RMM for Small and Medium Businesses (SMBs)
Network RMM (Remote Monitoring and Management) solutions are becoming increasingly popular among small and medium businesses (SMBs) due to their ability to simplify IT management, improve security, and reduce costs. These solutions offer a comprehensive approach to managing and monitoring IT infrastructure, providing a single platform for various tasks, including endpoint management, patch management, security monitoring, and more.
Benefits of Network RMM for SMBs
Network RMM solutions offer several benefits for SMBs, including:
- Improved Security: Network RMM solutions can help SMBs enhance their security posture by providing real-time monitoring of their network, identifying vulnerabilities, and automatically patching systems. This proactive approach helps reduce the risk of cyberattacks and data breaches.
- Reduced IT Costs: By automating tasks like software updates and system maintenance, Network RMM solutions can free up IT staff to focus on more strategic initiatives. This can lead to significant cost savings for SMBs.
- Increased Productivity: Network RMM solutions can help SMBs improve employee productivity by ensuring that their systems are running smoothly and efficiently. This can reduce downtime and improve the overall user experience.
- Improved IT Visibility: Network RMM solutions provide SMBs with a centralized view of their IT infrastructure, allowing them to monitor the health and performance of their systems. This visibility can help identify potential problems before they become major issues.
Addressing Unique Challenges Faced by SMBs
SMBs often face unique challenges when it comes to IT management, such as:
- Limited IT Resources: SMBs often have limited IT staff, making it difficult to manage their IT infrastructure effectively. Network RMM solutions can help alleviate this challenge by automating many tasks and providing a centralized platform for managing all IT assets.
- Budget Constraints: SMBs often have tight budgets, making it difficult to invest in expensive IT solutions. Network RMM solutions are available at a variety of price points, making them accessible to SMBs of all sizes.
- Security Concerns: SMBs are increasingly becoming targets of cyberattacks. Network RMM solutions can help SMBs mitigate these risks by providing comprehensive security monitoring and automated threat detection.
Choosing the Right Network RMM Solution for SMBs
When choosing a Network RMM solution, SMBs should consider the following factors:
- Features and Functionality: The solution should offer the features and functionality that are most important to the SMB, such as endpoint management, patch management, security monitoring, and reporting.
- Scalability: The solution should be scalable to meet the growing needs of the SMB. This is especially important for SMBs that are experiencing rapid growth.
- Ease of Use: The solution should be easy to use and manage, even for non-technical users. This will help ensure that the solution is adopted and used effectively by the SMB.
- Cost: The solution should be affordable for the SMB. SMBs should consider the total cost of ownership, including the initial purchase price, ongoing maintenance costs, and support fees.
Examples of Network RMM Solutions for SMBs
Several Network RMM solutions are specifically designed for SMBs, including:
- Atera: Atera is a cloud-based RMM solution that offers a wide range of features, including endpoint management, patch management, security monitoring, and ticketing. It is known for its ease of use and affordability.
- ConnectWise Manage: ConnectWise Manage is a comprehensive RMM solution that is popular among MSPs and SMBs. It offers a wide range of features, including automation, reporting, and integration with other IT tools.
- NinjaOne: NinjaOne is a cloud-based RMM solution that offers a wide range of features, including endpoint management, patch management, security monitoring, and ticketing. It is known for its user-friendly interface and its focus on automation.
Last Word
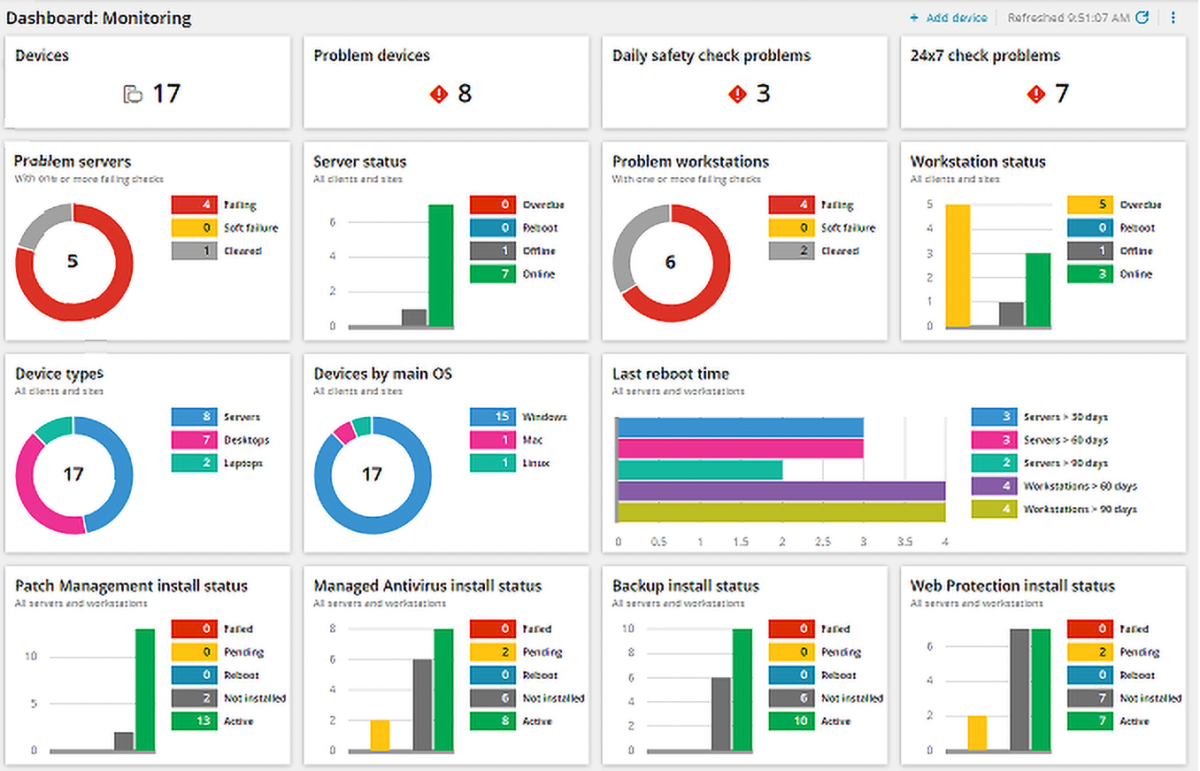
In today’s dynamic technological landscape, Network RMM has become an indispensable component of effective IT management. By embracing its capabilities, organizations can empower their IT teams, enhance security, and unlock new levels of operational efficiency, ultimately driving business success.
Network RMM, or Remote Monitoring and Management, is a powerful tool for managing IT infrastructure, but it’s important to have a reliable web browser for accessing the platform. Choosing the best web browser for your needs can significantly improve your RMM experience, ensuring smooth operation and efficient management of your network.
