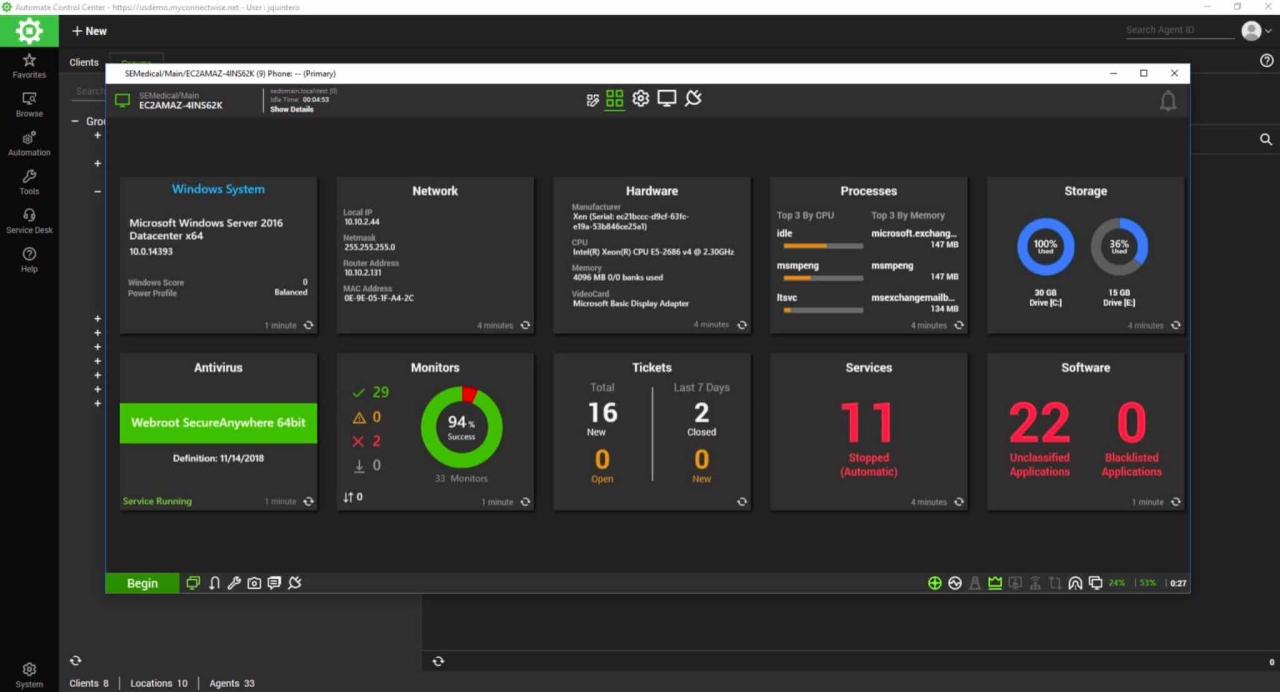
RMM monitoring is a crucial aspect of modern IT infrastructure management, providing a comprehensive approach to ensuring optimal system performance, security, and uptime. It empowers businesses to proactively identify and address potential issues before they impact operations, ultimately leading to improved efficiency and productivity.
Table of Contents
By leveraging automated tools and processes, RMM monitoring allows IT professionals to gain real-time insights into system health, performance, and security vulnerabilities. This data-driven approach enables informed decision-making, proactive maintenance, and swift incident response, minimizing downtime and maximizing operational efficiency.
What is RMM Monitoring?
RMM monitoring, short for Remote Monitoring and Management, is a powerful tool for IT professionals to remotely monitor and manage computer systems and networks. It provides a centralized platform for overseeing the health, performance, and security of devices, streamlining IT operations and reducing manual intervention.
Benefits of RMM Monitoring
RMM monitoring offers numerous benefits for businesses, including:
- Improved Efficiency: Automating routine tasks like software updates, patch management, and system backups saves time and effort for IT teams, freeing them to focus on more strategic initiatives.
- Enhanced Security: RMM monitoring proactively identifies and mitigates security threats, such as malware infections, unauthorized access, and data breaches, by providing real-time insights into system vulnerabilities and suspicious activity.
- Reduced Downtime: By detecting and addressing issues before they escalate, RMM monitoring minimizes downtime and ensures business continuity. Early identification of performance bottlenecks and hardware failures enables proactive troubleshooting and prevents disruptions to critical operations.
- Cost Savings: RMM monitoring streamlines IT processes, optimizes resource allocation, and reduces the need for on-site visits, leading to significant cost savings in the long run.
Examples of RMM Monitoring Enhancements
RMM monitoring can significantly enhance IT infrastructure management in various ways. Here are some examples:
- Proactive Patch Management: RMM tools can automatically identify and install critical software updates, ensuring that systems are protected from known vulnerabilities and security threats.
- Real-time Performance Monitoring: RMM monitoring provides continuous insights into system performance metrics, such as CPU utilization, memory usage, and disk space, allowing IT teams to identify and address performance bottlenecks proactively.
- Remote System Administration: RMM tools enable IT professionals to remotely manage and troubleshoot devices, eliminating the need for on-site visits and reducing response times for IT support requests.
- Automated Backup and Recovery: RMM monitoring can automate regular data backups, ensuring that critical data is protected and readily available in case of system failures or disasters.
Benefits of RMM Monitoring
RMM monitoring offers a comprehensive suite of benefits that can significantly enhance your IT infrastructure and operations. By providing real-time visibility and control over your systems, RMM monitoring helps streamline your IT processes, improve security, and boost overall efficiency.
Security Benefits
RMM monitoring plays a crucial role in safeguarding your IT infrastructure from various security threats. It acts as a proactive defense mechanism, detecting and preventing potential vulnerabilities before they can exploit your systems.
- Threat Detection: RMM monitoring tools continuously scan your network and endpoints for suspicious activity, including malware, ransomware, and unauthorized access attempts. These tools leverage advanced security features such as intrusion detection systems (IDS) and antivirus software to identify and alert you to potential threats in real-time.
- Vulnerability Assessment: Regular vulnerability assessments are critical for identifying and mitigating potential security risks. RMM monitoring tools automate this process, scanning your systems for known vulnerabilities and providing detailed reports on potential weaknesses. This allows you to proactively patch vulnerabilities and prevent exploitation.
- Security Policy Enforcement: RMM monitoring empowers you to enforce strict security policies across your entire network. You can set up automated rules to restrict unauthorized access, enforce password complexity requirements, and prevent the installation of malicious software. This ensures consistent security practices across all your devices.
System Performance and Uptime
RMM monitoring goes beyond security and helps optimize your system performance and ensure maximum uptime. By providing real-time insights into your system health, RMM tools enable you to proactively address performance issues and prevent downtime.
- Performance Monitoring: RMM monitoring tools track key performance indicators (KPIs) such as CPU utilization, memory usage, and disk space. This allows you to identify performance bottlenecks and resource constraints before they impact your system’s efficiency. You can then optimize resource allocation and prevent performance degradation.
- Proactive Maintenance: RMM monitoring empowers you to perform proactive maintenance tasks, such as software updates, driver installations, and system optimizations. By identifying potential issues early, you can prevent them from escalating into major problems that could cause downtime. This minimizes the risk of unexpected outages and ensures smooth system operation.
- Remote Troubleshooting: RMM monitoring allows you to remotely troubleshoot and resolve technical issues, even when you are not physically present at the user’s location. This significantly reduces downtime and improves service responsiveness. For example, you can diagnose and fix software errors, reboot systems, or provide remote support to users experiencing technical difficulties.
Benefits by Business Sector, Rmm monitoring
| Business Sector | Key Benefits of RMM Monitoring |
|---|---|
| Healthcare | Improved patient care through enhanced system reliability, secure data storage, and efficient medical device management. |
| Finance | Enhanced security measures to protect sensitive financial data, streamlined compliance with industry regulations, and improved customer service through remote support. |
| Education | Improved student learning through reliable access to educational resources, secure network environments, and efficient IT support for teachers and staff. |
| Retail | Enhanced customer experience through improved POS system reliability, streamlined inventory management, and secure payment processing. |
Types of RMM Monitoring Solutions
RMM monitoring solutions come in various forms, each with its own set of features, capabilities, and target audience. Understanding the different types of RMM monitoring solutions available in the market is crucial for making an informed decision about which one best suits your needs.
Comparison of RMM Monitoring Solutions
The types of RMM monitoring solutions can be categorized based on their deployment model, features, and target audience. Some common types include:
- On-Premises RMM: This type of RMM solution is installed and managed directly on your servers within your own data center. On-premises RMM offers high levels of control and customization, but it requires significant upfront investment in hardware and software, as well as ongoing maintenance and support.
- Cloud-Based RMM: This type of RMM solution is hosted and managed in the cloud, allowing you to access it from anywhere with an internet connection. Cloud-based RMM solutions are generally more affordable and easier to manage than on-premises solutions, but they may have limitations in terms of customization and control.
- Hybrid RMM: This type of RMM solution combines elements of both on-premises and cloud-based solutions. Hybrid RMM solutions can offer the best of both worlds, providing the flexibility and scalability of cloud solutions while maintaining some level of control and customization.
- Agentless RMM: This type of RMM solution does not require the installation of agents on the devices being monitored. Agentless RMM solutions are typically easier to deploy and manage, but they may have limited functionality compared to agent-based solutions.
- Agent-Based RMM: This type of RMM solution requires the installation of agents on the devices being monitored. Agent-based RMM solutions typically offer more comprehensive monitoring and management capabilities than agentless solutions, but they may be more complex to deploy and manage.
Key Factors to Consider When Choosing an RMM Monitoring Solution
Choosing the right RMM monitoring solution is essential for ensuring the security and performance of your IT infrastructure. Here are some key factors to consider when making your decision:
- Budget: RMM monitoring solutions can range in price from a few dollars per month to several hundred dollars per month. Consider your budget and choose a solution that offers the features and capabilities you need without breaking the bank.
- Features: Different RMM monitoring solutions offer different features. Consider your specific needs and choose a solution that provides the features you need, such as remote access, patch management, endpoint security, and reporting.
- Scalability: As your business grows, you may need to scale your RMM monitoring solution to accommodate more devices and users. Choose a solution that can easily scale to meet your future needs.
- Ease of Use: The RMM monitoring solution you choose should be easy to use and manage. Consider the technical skills of your IT staff and choose a solution that is intuitive and user-friendly.
- Support: Look for an RMM monitoring solution that provides excellent customer support. You want to be able to get help quickly and easily if you encounter any problems.
Cloud-Based vs. On-Premises RMM Monitoring Solutions
The choice between cloud-based and on-premises RMM monitoring solutions depends on your specific needs and preferences.
- Cloud-Based RMM:
- Pros:
- Cost-effective: Cloud-based RMM solutions are generally more affordable than on-premises solutions, as you don’t need to invest in hardware and software.
- Easy to deploy and manage: Cloud-based RMM solutions are typically easier to deploy and manage than on-premises solutions, as they are hosted and managed in the cloud.
- Scalable: Cloud-based RMM solutions can easily scale to meet your growing needs.
- Accessible from anywhere: You can access cloud-based RMM solutions from anywhere with an internet connection.
- Cons:
- Limited customization: Cloud-based RMM solutions may have limitations in terms of customization.
- Security concerns: Some organizations may be concerned about the security of their data in the cloud.
- Internet dependency: Cloud-based RMM solutions require an internet connection to function.
- Pros:
- On-Premises RMM:
- Pros:
- High levels of control and customization: On-premises RMM solutions offer high levels of control and customization, as you have complete control over your hardware and software.
- Enhanced security: On-premises RMM solutions can provide enhanced security, as your data is stored on your own servers.
- No internet dependency: On-premises RMM solutions do not require an internet connection to function.
- Cons:
- High upfront cost: On-premises RMM solutions require significant upfront investment in hardware and software.
- Complex to deploy and manage: On-premises RMM solutions can be complex to deploy and manage, as you need to have the necessary technical expertise.
- Limited scalability: On-premises RMM solutions may be more difficult to scale than cloud-based solutions.
- Pros:
Implementation of RMM Monitoring
Implementing an RMM monitoring solution can seem daunting, but it’s a crucial step toward optimizing your IT infrastructure and ensuring its smooth operation. This section Artikels the key stages of implementation, providing a clear roadmap to guide you through the process.
Integrating RMM Monitoring with Existing IT Infrastructure
Integrating an RMM monitoring solution with your existing IT infrastructure is a critical step. This process involves connecting the RMM tool to your network, devices, and applications to gather real-time data for analysis and reporting.
- Network Integration: The first step is to configure the RMM tool to access your network. This might involve setting up a dedicated agent on your network devices, such as routers and switches, to collect data on network performance and traffic patterns. You can use techniques like SNMP (Simple Network Management Protocol) or WMI (Windows Management Instrumentation) for this purpose.
- Device Integration: Next, you need to install agents on individual devices, like computers, servers, and mobile devices. These agents gather data on hardware and software usage, performance metrics, and security vulnerabilities. Ensure the RMM tool supports your operating systems and device types.
- Application Integration: For specific applications, you might need to integrate the RMM tool with application monitoring tools or APIs. This allows you to track application performance, availability, and user activity.
Configuring and Customizing RMM Monitoring Tools
Once your RMM tool is integrated, you need to configure it to meet your specific needs. This involves defining monitoring parameters, setting up alerts, and customizing reports.
- Monitoring Parameters: You need to specify the metrics you want to monitor for each device and application. For example, you might track CPU usage, memory consumption, disk space, and network bandwidth.
- Alerting: Set up alerts to notify you when specific thresholds are exceeded. For example, you can receive email notifications when CPU usage reaches 90% or when disk space falls below a certain limit.
- Reporting: Customize reports to provide insights into your IT infrastructure’s performance and health. You can create reports that show historical trends, identify bottlenecks, and highlight potential issues.
Best Practices for Implementing RMM Monitoring
Successful implementation of RMM monitoring requires careful planning and adherence to best practices. Here are some key considerations:
- Start Small: Begin with monitoring a small number of critical devices and applications. This allows you to familiarize yourself with the RMM tool and its capabilities before expanding monitoring to your entire infrastructure.
- Prioritize Monitoring: Focus on monitoring the most critical components of your IT infrastructure. This might include servers, databases, and applications that are essential for your business operations.
- Regularly Review and Adjust: As your IT environment evolves, you need to regularly review and adjust your RMM monitoring configuration. This ensures that your monitoring solution remains effective and relevant to your changing needs.
- Use a Phased Approach: Implementing RMM monitoring doesn’t have to be a single, all-encompassing project. You can adopt a phased approach, starting with basic monitoring and gradually adding more features and complexity as your team gains experience and confidence.
Alerting and Reporting
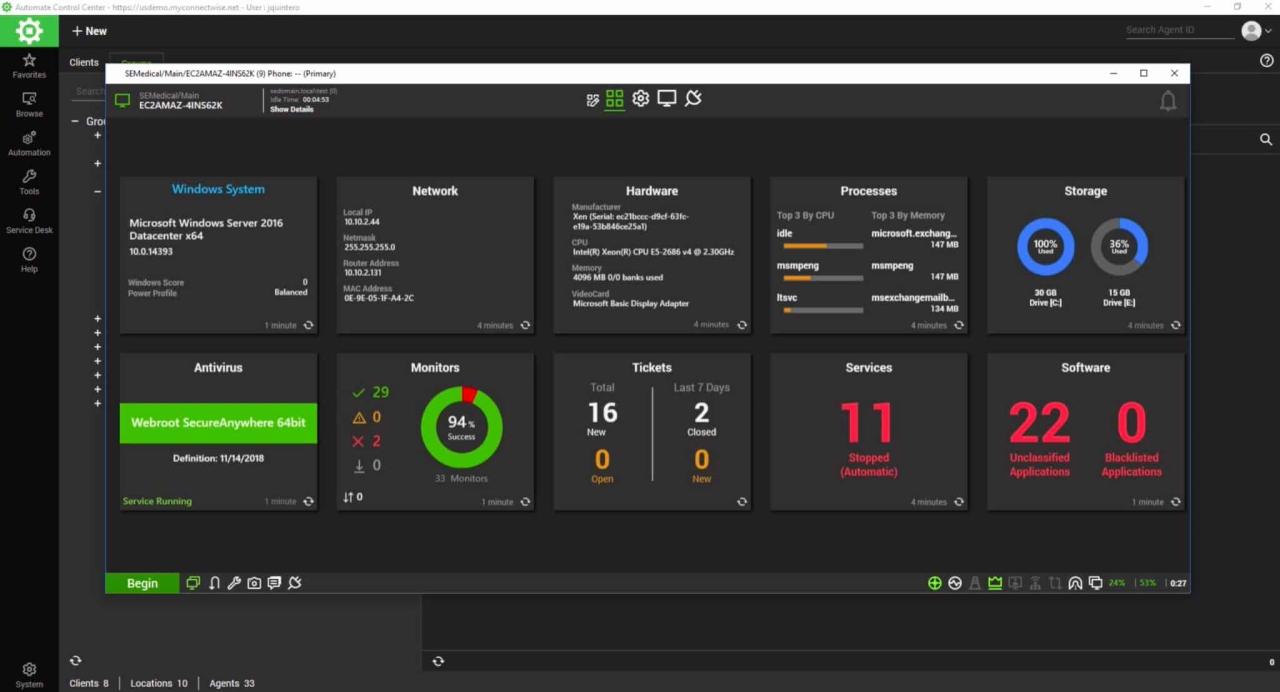
RMM monitoring tools provide valuable insights into the health and performance of your IT infrastructure. However, the true power of RMM lies in its ability to alert you to potential issues and generate comprehensive reports that help you make informed decisions.
Types of Alerts and Reports
RMM tools generate a wide range of alerts and reports to help you stay informed about the state of your IT environment. Here are some common examples:
- System Health Alerts: These alerts notify you of critical issues such as server downtime, hard drive failures, or software crashes. These alerts are essential for ensuring business continuity and minimizing downtime.
- Security Alerts: Security alerts inform you of potential threats such as malware infections, unauthorized access attempts, or suspicious network activity. These alerts help you protect your data and systems from malicious attacks.
- Performance Alerts: Performance alerts trigger when your systems are experiencing performance issues such as slow response times, high CPU utilization, or network bottlenecks. These alerts help you identify and address performance bottlenecks before they impact user productivity.
- Patching and Updates Alerts: Patching and updates alerts notify you when critical security patches or software updates are available for your systems. These alerts help you keep your systems secure and up-to-date.
- Inventory Reports: Inventory reports provide a comprehensive overview of your IT assets, including hardware, software, and licenses. These reports are essential for managing your IT infrastructure effectively.
- Security Reports: Security reports provide detailed information about your security posture, including vulnerability assessments, threat detection logs, and incident response summaries. These reports help you identify and address security vulnerabilities.
- Performance Reports: Performance reports provide insights into the performance of your systems and applications. These reports can include metrics such as CPU utilization, memory usage, network bandwidth, and response times. They help you identify and address performance bottlenecks and optimize system performance.
Proactive Issue Identification and Resolution
RMM alerts and reports empower you to proactively identify and address potential issues before they escalate into major problems. By monitoring your systems in real-time and receiving timely alerts, you can:
- Identify and resolve issues quickly: RMM alerts provide immediate notification of potential problems, allowing you to take action before they impact your users or business operations.
- Prevent downtime: By addressing issues early, you can prevent system failures and downtime, ensuring business continuity.
- Improve system performance: RMM alerts can help you identify and address performance bottlenecks, improving system responsiveness and user productivity.
- Enhance security posture: Security alerts can help you detect and respond to threats quickly, reducing the risk of data breaches and other security incidents.
IT Service Management and Decision-Making
RMM reporting plays a crucial role in improving IT service management and decision-making. By providing comprehensive insights into the health, performance, and security of your IT infrastructure, RMM reports can help you:
- Optimize resource allocation: RMM reports provide insights into system usage patterns, allowing you to allocate resources effectively and reduce waste.
- Improve service delivery: By identifying and addressing performance bottlenecks, you can improve service delivery and enhance user satisfaction.
- Make informed investment decisions: RMM reports can help you identify areas where investments in new hardware, software, or security measures are needed.
- Demonstrate IT value: RMM reports provide data that can be used to demonstrate the value of your IT services to stakeholders.
Case Studies and Real-World Examples
RMM monitoring has proven to be a game-changer for businesses across various industries. Implementing RMM solutions has yielded significant improvements in IT efficiency, security, and overall performance. This section delves into real-world examples of how businesses have successfully leveraged RMM monitoring and the positive impact it has had on their operations.
Impact on IT Efficiency
The following case studies highlight the transformative power of RMM monitoring in streamlining IT operations and enhancing efficiency:
- A large healthcare provider implemented RMM monitoring to automate routine tasks, such as software updates and patch management. This freed up IT staff to focus on more strategic initiatives, resulting in a 20% reduction in downtime and a 15% increase in employee productivity.
- A financial services company utilized RMM monitoring to remotely manage and monitor their entire network, reducing the need for on-site visits and minimizing service disruptions. This resulted in a 30% decrease in support costs and a 10% increase in customer satisfaction.
Enhanced Security Posture
RMM monitoring has been instrumental in bolstering security posture and mitigating cyber threats:
- An educational institution implemented RMM monitoring to proactively detect and respond to security vulnerabilities. This led to a 50% reduction in security incidents and a significant improvement in data protection.
- A manufacturing company utilized RMM monitoring to enforce security policies and identify potential malware infections. This resulted in a 75% decrease in malware attacks and a significant improvement in overall security posture.
Improved Performance and Reliability
RMM monitoring has played a vital role in optimizing performance and ensuring system reliability:
- A retail company implemented RMM monitoring to track server performance and identify potential bottlenecks. This enabled them to optimize resource allocation, resulting in a 15% increase in server uptime and a 10% improvement in application performance.
- A technology firm utilized RMM monitoring to monitor network performance and identify potential issues. This allowed them to proactively address problems, resulting in a 20% reduction in network outages and a 15% improvement in network reliability.
Key Lessons Learned
The case studies demonstrate several key lessons that are relevant to organizations of all sizes:
- Proactive monitoring is crucial: RMM monitoring allows organizations to identify and address potential issues before they escalate into major problems, minimizing downtime and service disruptions.
- Automation is key: RMM monitoring automates routine tasks, freeing up IT staff to focus on more strategic initiatives and improving overall efficiency.
- Data-driven decision-making: RMM monitoring provides valuable data that can be used to make informed decisions about IT investments, resource allocation, and security policies.
- Scalability and flexibility: RMM solutions are scalable and flexible, allowing organizations to adapt to changing needs and business requirements.
End of Discussion
In conclusion, RMM monitoring is an indispensable tool for businesses seeking to optimize their IT infrastructure and ensure seamless operations. By embracing automated monitoring, proactive maintenance, and robust security measures, organizations can achieve significant improvements in system performance, security posture, and overall IT efficiency. The benefits of RMM monitoring extend across various business sectors, enabling organizations to confidently navigate the complexities of today’s digital landscape.
RMM monitoring helps ensure the smooth operation of your systems by keeping an eye on key metrics. For example, if you’re running simulations with LAMMPS , an open-source molecular dynamics simulator, RMM can help you monitor CPU usage, memory consumption, and other performance indicators.
This allows you to identify potential bottlenecks and optimize your simulations for maximum efficiency.