Top 10 RMM software takes center stage, offering a comprehensive approach to streamlining your IT operations. RMM (Remote Monitoring and Management) solutions have become indispensable for businesses of all sizes, providing a centralized platform to monitor, manage, and secure their IT infrastructure. These powerful tools empower IT teams to proactively address issues, improve efficiency, and enhance overall system performance.
Table of Contents
From automated patch management and endpoint security to remote access and software deployment, RMM software empowers IT professionals to manage their infrastructure with ease. Whether you’re a small business owner or a large enterprise, implementing RMM can significantly enhance your IT operations, freeing up valuable time and resources for strategic initiatives.
Introduction to RMM Software
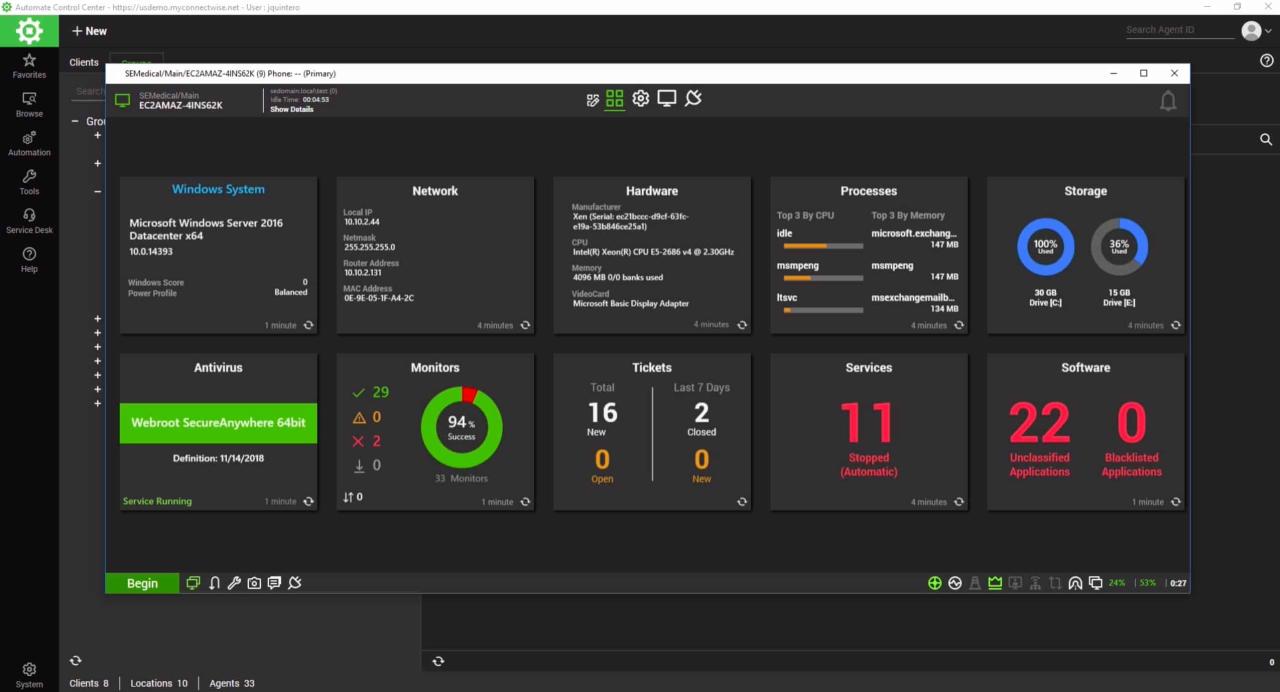
RMM (Remote Monitoring and Management) software is a crucial tool for IT departments and Managed Service Providers (MSPs) to effectively manage and monitor IT infrastructure remotely. It empowers organizations to streamline their IT operations, improve efficiency, and ensure the security and stability of their systems.
RMM software plays a vital role in managing IT systems by providing a centralized platform for monitoring, managing, and automating various IT tasks. This software allows IT professionals to remotely access and control devices, proactively identify and resolve issues, and ensure the smooth functioning of the IT environment.
Key Features and Functionalities of RMM Solutions
RMM solutions offer a comprehensive set of features designed to simplify and enhance IT management. Here are some key functionalities:
- Remote Access and Control: RMM software enables IT professionals to access and control devices remotely, regardless of their physical location. This allows for quick troubleshooting, software deployment, and configuration changes.
- System Monitoring: RMM solutions continuously monitor critical system parameters, such as CPU usage, memory consumption, disk space, and network activity. This proactive monitoring helps identify potential issues before they escalate into major problems.
- Patch Management: RMM software automates the process of applying software updates and security patches to devices. This ensures that systems are up-to-date with the latest security fixes, reducing the risk of vulnerabilities.
- Security and Compliance: RMM solutions incorporate security features to protect devices from malware, unauthorized access, and other threats. They can enforce security policies, monitor user activity, and provide real-time threat detection.
- Reporting and Analytics: RMM software generates detailed reports on system performance, security events, and other relevant metrics. These reports provide valuable insights into IT infrastructure health and identify areas for improvement.
- Automation and Scripting: RMM solutions support automation and scripting capabilities, allowing IT professionals to automate repetitive tasks, such as backups, software installations, and system maintenance.
Common Use Cases for RMM Software
RMM software finds applications across various industries, providing solutions to common IT management challenges. Here are some examples:
- Healthcare: RMM software is used to manage medical devices, electronic health records (EHRs), and patient data. It ensures compliance with HIPAA regulations and maintains the integrity of sensitive patient information.
- Financial Services: RMM solutions help financial institutions manage critical systems, comply with industry regulations, and protect sensitive customer data. They ensure the availability of financial services and prevent data breaches.
- Education: RMM software is used in educational institutions to manage student devices, network infrastructure, and learning platforms. It ensures secure access to educational resources and provides remote support to students and faculty.
- Manufacturing: RMM solutions are used in manufacturing companies to manage industrial control systems, production lines, and data collection systems. They ensure operational efficiency, prevent downtime, and optimize production processes.
Benefits of Using RMM Software
RMM software offers a multitude of advantages for businesses of all sizes, streamlining IT operations, enhancing security, and ultimately saving costs. By automating routine tasks, providing centralized control, and offering valuable insights, RMM solutions empower organizations to optimize their IT infrastructure and achieve significant improvements in efficiency and security.
Increased IT Efficiency
RMM software significantly enhances IT efficiency by automating routine tasks and simplifying complex processes. This frees up IT professionals to focus on more strategic initiatives, leading to improved productivity and overall efficiency.
- Automated Patch Management: RMM software automatically updates systems and applications with the latest security patches, eliminating the manual effort required for patch management and minimizing vulnerabilities.
- Remote Monitoring and Management: RMM enables IT teams to monitor and manage devices remotely, reducing the need for on-site visits and minimizing downtime. This allows for proactive issue identification and resolution, preventing potential problems before they impact operations.
- Simplified Asset Management: RMM solutions provide a comprehensive view of all IT assets, including hardware, software, and licenses. This centralized inventory management system facilitates efficient tracking, licensing compliance, and cost optimization.
Enhanced Security
RMM software plays a crucial role in bolstering cybersecurity by providing real-time threat detection, automated vulnerability assessment, and proactive security measures.
- Real-Time Threat Detection: RMM solutions monitor systems for suspicious activity and potential security threats, providing early warnings and allowing for prompt response. This proactive approach helps mitigate the risk of data breaches and malware infections.
- Automated Vulnerability Assessment: RMM software automatically scans devices for vulnerabilities and provides detailed reports, enabling IT teams to prioritize and address security weaknesses. This continuous assessment ensures a proactive security posture, reducing the likelihood of successful attacks.
- Endpoint Security Management: RMM solutions offer centralized control over endpoint security settings, enabling the implementation of consistent security policies across all devices. This includes features like antivirus protection, firewall management, and data loss prevention, ensuring comprehensive endpoint security.
Cost Savings
RMM software helps businesses achieve significant cost savings by optimizing IT operations, reducing downtime, and minimizing security risks.
- Reduced IT Labor Costs: By automating routine tasks, RMM software frees up IT professionals to focus on more strategic projects, reducing the need for additional staff and associated labor costs. This allows organizations to optimize their IT budget and allocate resources more effectively.
- Minimized Downtime: RMM solutions enable proactive issue identification and resolution, minimizing downtime and its associated costs. This includes reducing the impact of system failures, application crashes, and security breaches, ultimately improving business continuity and productivity.
- Improved Security Posture: RMM software’s security features help mitigate the risk of data breaches and cyberattacks, reducing the potential costs associated with data recovery, regulatory fines, and reputational damage. This proactive approach helps organizations avoid costly security incidents and maintain a strong security posture.
Real-World Examples
- Small Business Success Story: A small retail business implemented RMM software to automate routine tasks like patch management and remote monitoring. This freed up their IT administrator to focus on improving customer service and developing new sales strategies, resulting in a significant increase in sales and customer satisfaction.
- Enterprise Security Improvement: A large financial institution implemented RMM software to enhance their security posture and mitigate the risk of cyberattacks. The solution’s automated vulnerability assessment and real-time threat detection capabilities enabled them to identify and address security vulnerabilities promptly, preventing a major data breach and safeguarding sensitive customer information.
Key Considerations for Choosing RMM Software
Choosing the right RMM software is crucial for ensuring the smooth operation and security of your IT infrastructure. It involves evaluating various factors to determine the best fit for your specific needs.
Pricing
Pricing is a significant factor to consider when choosing RMM software. Different vendors offer various pricing models, including per-device, per-technician, or tiered pricing based on the number of managed devices.
- It is important to assess your budget and choose a pricing model that aligns with your financial constraints and the number of devices you need to manage.
- Consider the long-term cost implications, including any additional fees for features, support, or training.
Features
The features offered by RMM software can significantly impact its effectiveness in managing your IT infrastructure. Essential features include remote access, patch management, endpoint security, asset management, and reporting.
- Evaluate the specific features offered by each vendor and prioritize those that align with your organization’s needs.
- Consider the depth and breadth of the features offered, as well as the ease of use and customization options.
Scalability
Scalability refers to the ability of the RMM software to handle an increasing number of devices and users without compromising performance. As your organization grows, it is essential to choose software that can scale with your needs.
- Consider the software’s ability to handle a growing number of devices and users without impacting performance.
- Evaluate the vendor’s track record in supporting large-scale deployments and their ability to provide timely and efficient support.
Integration Capabilities
Integration capabilities refer to the software’s ability to seamlessly connect with other tools and systems used in your IT infrastructure. This includes integration with ticketing systems, monitoring tools, and other IT management solutions.
- Assess the software’s compatibility with your existing IT infrastructure and the integration options available.
- Prioritize vendors that offer seamless integration with your existing tools and systems to minimize disruption and maximize efficiency.
Compatibility with Existing IT Infrastructure
Compatibility with your existing IT infrastructure is essential for ensuring a smooth transition and minimizing disruption. This includes compatibility with operating systems, hardware, and other software applications.
- Verify that the RMM software is compatible with your existing operating systems, hardware, and other software applications.
- Consider the vendor’s support for different platforms and versions to ensure compatibility with your current and future IT environment.
Support Services
Support services are crucial for ensuring the successful implementation and ongoing operation of the RMM software. This includes technical support, training, and documentation.
- Evaluate the vendor’s support services, including response times, availability, and expertise.
- Consider the availability of training resources and documentation to facilitate the adoption and use of the software.
Checklist of Questions to Ask Potential RMM Vendors
When evaluating potential RMM vendors, it is essential to ask specific questions to understand their capabilities and suitability for your needs. Here are some key questions to consider:
- What pricing models do you offer, and what are the costs associated with different features and levels of support?
- What features are included in your RMM software, and how do they address our specific needs?
- How scalable is your software, and what is your experience in supporting large-scale deployments?
- What integration options are available, and how do they work with our existing IT infrastructure?
- What support services do you provide, and what are your response times and availability?
- Can you provide references from other organizations that have successfully implemented your RMM software?
- What is your security posture, and how do you ensure the protection of sensitive data?
- What is your roadmap for future development, and how will it impact our use of the software?
Top 10 RMM Software Solutions
Choosing the right RMM software can be a daunting task, with so many options available. This list presents ten of the most popular and effective RMM solutions, highlighting their key features, pricing models, and target audience.
Top 10 RMM Software Solutions
| Name | Key Features | Pricing Model | Target Audience |
|---|---|---|---|
| Atera | Remote access, patch management, endpoint security, ticketing system, reporting | Subscription-based, starting at $79 per month | Small to medium-sized businesses (SMBs) |
| ConnectWise Automate | Comprehensive automation, scripting, patch management, remote control, endpoint security | Subscription-based, starting at $199 per month | Managed service providers (MSPs) and IT departments |
| Datto RMM | Endpoint management, security, and backup, remote access, patch management | Subscription-based, pricing varies by features and number of devices | MSPs and IT departments |
| NinjaOne | Remote access, endpoint management, patch management, security, ticketing system | Subscription-based, starting at $59 per month | MSPs and IT departments |
| N-able N-central | Comprehensive automation, scripting, patch management, remote control, endpoint security | Subscription-based, pricing varies by features and number of devices | MSPs and IT departments |
| Pulseway | Remote access, endpoint management, patch management, security, reporting | Subscription-based, starting at $39 per month | MSPs and IT departments |
| SolarWinds MSP | Remote access, endpoint management, patch management, security, reporting | Subscription-based, starting at $49 per month | MSPs and IT departments |
| TeamViewer Tensor | Remote access, endpoint management, patch management, security, reporting | Subscription-based, starting at $49 per month | MSPs and IT departments |
| Zoho ManageEngine | Remote access, endpoint management, patch management, security, reporting | Subscription-based, starting at $25 per month | SMBs and IT departments |
| Auvik | Network monitoring, device management, reporting, and troubleshooting | Subscription-based, pricing varies by features and number of devices | MSPs and IT departments |
Comparison of Leading RMM Solutions
Choosing the right RMM solution can be a daunting task, as many options cater to different needs and budgets. To simplify the decision-making process, we’ll compare and contrast three leading RMM solutions based on their features, pricing, user experience, and customer support.
Comparison Table
This table highlights key features and aspects of three leading RMM solutions:
| Feature | Atera | NinjaOne | ConnectWise Automate |
|---|---|---|---|
| Pricing | Starts at $79/month for 10 devices | Starts at $49/month for 10 devices | Starts at $149/month for 10 devices |
| Features | Remote access, patch management, software deployment, endpoint monitoring, scripting, reporting | Remote access, patch management, software deployment, endpoint monitoring, scripting, reporting, ticketing system, asset management | Remote access, patch management, software deployment, endpoint monitoring, scripting, reporting, ticketing system, asset management, PSA integration |
| User Experience | Intuitive and user-friendly interface, mobile app available | Clean and modern interface, mobile app available | More complex interface, requires some technical expertise |
| Customer Support | 24/7 phone, email, and chat support | 24/7 phone, email, and chat support | 24/7 phone, email, and chat support, dedicated account manager |
Detailed Analysis of Strengths and Weaknesses
- Atera: Atera is a popular choice for its affordability and user-friendly interface. It offers a wide range of features, including remote access, patch management, and endpoint monitoring. Atera’s strengths lie in its ease of use and its robust scripting capabilities. However, its lack of PSA integration might be a drawback for some businesses.
- NinjaOne: NinjaOne stands out for its comprehensive suite of features, including a built-in ticketing system and asset management. It also offers a clean and modern interface, making it a good choice for businesses seeking a user-friendly experience. While NinjaOne is a feature-rich solution, its pricing can be higher than some competitors.
- ConnectWise Automate: ConnectWise Automate is a powerful and feature-rich RMM solution that offers extensive functionality, including PSA integration and advanced reporting. It caters to larger businesses with complex IT environments. However, its complex interface might require some technical expertise, and its pricing is higher than Atera and NinjaOne.
Unique Selling Propositions
- Atera: Atera’s unique selling proposition is its affordability and user-friendly interface, making it an accessible solution for small and medium-sized businesses. Its intuitive design and robust scripting capabilities contribute to its popularity.
- NinjaOne: NinjaOne’s unique selling proposition lies in its comprehensive feature set, including a built-in ticketing system and asset management. Its clean and modern interface further enhances its user experience.
- ConnectWise Automate: ConnectWise Automate’s unique selling proposition is its advanced functionality, including PSA integration and extensive reporting capabilities. This makes it suitable for larger businesses with complex IT environments.
Integration with Other IT Tools
RMM software is designed to simplify and automate various IT management tasks. However, its effectiveness can be significantly amplified when integrated with other IT tools. Seamless integration with tools like ticketing systems, monitoring software, and security solutions can streamline workflows, enhance efficiency, and provide a comprehensive view of the IT environment.
Benefits of Integration
The integration of RMM software with other IT tools offers numerous benefits, leading to a more efficient and effective IT management approach.
- Centralized Management: Integrating RMM with other tools creates a central hub for managing various IT functions. This eliminates the need to switch between multiple platforms, simplifying administration and providing a unified view of the IT landscape.
- Automated Workflows: Integration allows for the automation of tasks and processes across different IT tools. For example, an RMM tool can automatically create a ticket in a ticketing system when a device reports a critical error, ensuring timely issue resolution.
- Improved Collaboration: Integrating RMM with communication and collaboration tools enables teams to work together more effectively. For instance, technicians can directly access relevant information from the RMM tool within their communication platform, facilitating faster issue resolution.
- Enhanced Security: Integration with security solutions can strengthen the overall security posture of the IT environment. RMM tools can receive security alerts from other tools, enabling proactive threat detection and mitigation.
- Increased Visibility: Integrating RMM with monitoring tools provides comprehensive visibility into the IT infrastructure. This allows IT teams to identify potential issues before they become major problems, improving system stability and reducing downtime.
Examples of Successful Integrations
- RMM and Ticketing Systems: Integrating an RMM tool with a ticketing system like Zendesk or Freshdesk enables automated ticket creation for detected issues. This streamlines the help desk process, ensuring faster resolution times and improved user satisfaction.
- RMM and Monitoring Software: Integration with monitoring tools like Datadog or New Relic provides real-time performance data, allowing RMM tools to proactively address potential issues before they impact system performance.
- RMM and Security Solutions: Integrating RMM with security solutions like Sophos or Symantec allows for centralized security management and automated remediation of vulnerabilities. This enhances the overall security posture of the IT environment.
Security Considerations in RMM Software
RMM software is designed to manage and secure your IT infrastructure, but it’s important to remember that the software itself must also be secure. Choosing an RMM solution with robust security features is essential to protect your data and prevent unauthorized access to your systems.
Data Encryption
Data encryption is crucial for protecting sensitive information from unauthorized access. RMM software should encrypt data both in transit and at rest. This means that data is encrypted when it’s being transferred between devices and when it’s stored on the RMM server.
- Look for RMM solutions that use industry-standard encryption algorithms, such as AES-256.
- Ensure that the encryption keys are securely stored and managed.
- Confirm that the RMM provider has a strong security policy and is compliant with relevant data privacy regulations.
Access Control, Top 10 rmm software
Access control mechanisms help ensure that only authorized personnel can access your RMM system and the data it manages. RMM software should provide granular access control features, allowing you to assign different levels of permissions to different users.
- Use multi-factor authentication (MFA) to enhance account security. MFA requires users to provide two or more forms of authentication, such as a password and a one-time code from a mobile app.
- Implement role-based access control (RBAC) to assign permissions based on user roles. This ensures that users only have access to the information and resources they need to perform their jobs.
- Regularly audit user activity to identify any suspicious or unauthorized behavior.
Vulnerability Management
RMM software should have built-in vulnerability management capabilities to help you identify and remediate security vulnerabilities on your systems.
- Choose an RMM solution that integrates with vulnerability scanning tools to automate the process of identifying vulnerabilities.
- The RMM software should provide detailed reports on identified vulnerabilities, including severity levels and recommended remediation steps.
- The RMM software should allow you to prioritize vulnerability remediation based on risk level and impact.
Deployment and Implementation of RMM Software
Successfully deploying and implementing RMM software is crucial for maximizing its benefits and achieving your desired IT management outcomes. This process requires careful planning, configuration, and user training to ensure a smooth transition and seamless integration into your existing IT infrastructure.
Planning for RMM Deployment
Planning is the cornerstone of a successful RMM deployment. It involves defining your objectives, identifying the scope of the implementation, and establishing a clear roadmap for the entire process.
- Define your objectives: Clearly articulate what you aim to achieve with the RMM solution. This could include improving system performance, enhancing security, automating tasks, or streamlining IT operations. Defining your objectives helps you select the right RMM software and prioritize features.
- Determine the scope: Identify the specific devices, users, and systems you want to include in the RMM deployment. This helps you determine the required licenses and assess the complexity of the implementation.
- Develop a deployment plan: Create a detailed plan outlining the steps involved, timelines, and responsibilities. This plan should include tasks such as data migration, user training, and system testing.
- Establish a communication strategy: Keep stakeholders informed about the progress of the deployment. Communicate updates, address concerns, and provide training materials to ensure a smooth transition.
Configuring the RMM Software
After planning, the next step is to configure the RMM software to meet your specific needs. This involves customizing settings, integrating with other IT tools, and establishing policies for managing endpoints.
- Install and configure the RMM server: Set up the RMM server in your environment, ensuring it meets the necessary hardware and software requirements. Configure network settings, security protocols, and other essential parameters.
- Define policies and rules: Establish policies for managing endpoints, including software updates, security settings, and user access. These policies should align with your organization’s IT security and compliance requirements.
- Integrate with existing tools: Connect the RMM software with other IT tools you use, such as ticketing systems, monitoring platforms, or identity management solutions. This enables seamless data flow and centralized management.
- Test and validate configuration: Thoroughly test the RMM software configuration to ensure it functions as expected and meets your requirements. This includes verifying policies, monitoring performance, and identifying any potential issues.
User Training and Support
Providing adequate user training is essential for ensuring the successful adoption of the RMM solution. This involves educating users on how to use the software, navigate its features, and troubleshoot common issues.
- Develop training materials: Create user-friendly documentation, tutorials, and online resources to guide users through the RMM software’s features and functionalities.
- Conduct hands-on training sessions: Organize interactive training sessions to provide users with practical experience using the RMM software. This allows them to ask questions and receive immediate support.
- Offer ongoing support: Provide ongoing support to users after the deployment. This could include answering questions, resolving issues, and offering guidance on best practices for using the RMM solution.
- Create a knowledge base: Establish a centralized repository for user guides, FAQs, and troubleshooting tips. This allows users to access information quickly and efficiently.
Tips for Successful RMM Rollout
Following these tips can enhance the success of your RMM deployment and ensure a smooth transition.
- Start with a pilot program: Deploy the RMM solution on a small group of devices or users to test its functionality and identify any potential issues before rolling it out to the entire organization.
- Communicate effectively: Keep stakeholders informed about the deployment process, providing regular updates, addressing concerns, and gathering feedback.
- Prioritize security: Implement robust security measures to protect sensitive data and ensure compliance with industry regulations. This includes using strong passwords, encrypting data, and regularly updating security patches.
- Monitor and optimize performance: Continuously monitor the RMM solution’s performance, identify bottlenecks, and optimize settings to ensure efficient and reliable operation.
- Seek expert assistance: Consider engaging a qualified IT consultant or managed service provider to assist with the deployment and ongoing management of the RMM solution. Their expertise can help ensure a smooth and successful implementation.
Future Trends in RMM Software
The landscape of RMM software is constantly evolving, driven by technological advancements and the growing demand for efficient IT management solutions. As we move forward, several key trends will shape the future of RMM software, influencing how businesses manage their IT infrastructure and security.
The Impact of Artificial Intelligence and Machine Learning
The integration of AI and ML into RMM solutions is revolutionizing how IT issues are detected, diagnosed, and resolved. These technologies can analyze vast amounts of data from devices and networks to identify patterns and predict potential problems before they arise. This proactive approach to IT management can significantly reduce downtime and improve overall system performance.
- Predictive Maintenance: AI-powered RMM solutions can analyze historical data on device performance, usage patterns, and environmental factors to predict potential failures and schedule preventative maintenance. This proactive approach minimizes downtime and extends the lifespan of IT assets.
- Automated Incident Response: AI can automate incident response processes, enabling faster and more efficient resolution of IT issues. By analyzing data from multiple sources, AI can identify the root cause of problems and recommend appropriate solutions, reducing manual effort and improving response times.
- Security Threat Detection: AI-powered security tools can analyze network traffic, user behavior, and other data sources to identify potential threats and vulnerabilities. This proactive approach to security can help organizations prevent breaches and protect sensitive data.
Increased Automation and Integration
The future of RMM software lies in increased automation and seamless integration with other IT tools. This trend aims to simplify IT management by streamlining processes and reducing manual tasks.
- Automated Patch Management: RMM solutions can automate the process of identifying, downloading, and applying security patches to all devices in a network. This ensures that systems are always up-to-date with the latest security fixes, reducing the risk of vulnerabilities and breaches.
- Integration with Other IT Tools: RMM solutions are increasingly integrating with other IT tools, such as ticketing systems, monitoring platforms, and cloud services. This integration allows for a more unified approach to IT management, enabling organizations to manage their entire IT infrastructure from a single platform.
- Workflow Automation: RMM solutions can automate repetitive tasks, such as user provisioning, software deployment, and data backups. This frees up IT professionals to focus on more strategic initiatives, improving overall efficiency and productivity.
Focus on Cybersecurity and Compliance
As cyber threats continue to evolve, RMM software will play an increasingly crucial role in helping organizations protect their IT infrastructure and comply with industry regulations.
- Enhanced Security Features: RMM solutions are incorporating advanced security features, such as endpoint detection and response (EDR), threat intelligence, and vulnerability scanning, to protect against sophisticated cyberattacks.
- Compliance Automation: RMM solutions can help organizations automate compliance tasks, such as security audits, data backups, and access control. This simplifies compliance efforts and reduces the risk of penalties.
- Data Privacy and Security: RMM software providers are prioritizing data privacy and security by implementing robust encryption protocols, access controls, and data retention policies.
The Rise of Cloud-Based RMM Solutions
Cloud-based RMM solutions are becoming increasingly popular due to their scalability, accessibility, and cost-effectiveness.
- Scalability and Flexibility: Cloud-based RMM solutions can easily scale to meet the needs of growing businesses, providing access to resources and functionality on demand. This flexibility allows organizations to adapt to changing IT requirements without investing in expensive hardware.
- Accessibility and Collaboration: Cloud-based RMM solutions are accessible from anywhere with an internet connection, enabling IT teams to manage devices and networks remotely. This improves collaboration and communication within IT teams, regardless of location.
- Cost-Effectiveness: Cloud-based RMM solutions eliminate the need for expensive hardware and software licenses, reducing overall IT costs. The pay-as-you-go model also provides organizations with greater control over their IT budget.
The Future of RMM: A Proactive and Intelligent Approach to IT Management
The future of RMM software is characterized by a proactive and intelligent approach to IT management. AI, ML, and automation will empower organizations to anticipate and prevent IT issues, optimize system performance, and enhance security. This shift towards a more proactive and intelligent approach to IT management will ultimately lead to greater efficiency, reduced downtime, and improved business outcomes.
Summary
Navigating the world of RMM software can be overwhelming, but with careful consideration of your specific needs and a thorough evaluation of the top contenders, you can choose a solution that perfectly aligns with your IT goals. Whether you prioritize security, cost-effectiveness, or user-friendliness, the right RMM software can empower your IT team to excel, optimize your infrastructure, and drive your business forward.
Finding the right RMM software can be a challenge, especially with so many options available. You’ll want to consider features like remote control, patch management, and security monitoring. Some RMM solutions also offer remote desktop monitoring software as part of their suite, which can be a valuable addition for managing and troubleshooting client devices.
When choosing your top 10 RMM software, be sure to prioritize the features that are most important for your needs.
